Let's see how we can help you!
Leave a message and our dedicated advisor will contact you.
Send us a message
0/10000
Leave a message and our dedicated advisor will contact you.

The contemporary cybersecurity threat landscape has transformed into a dynamic jungle where traditional defensive approaches are no longer effective. Digital transformation, cloud computing, remote work, the Internet of Things (IoT), and complex supply chains have scattered the boundaries of traditional IT infrastructure. The classic "castle and moat" approach—where the firewall constituted the perimeter and we sat safely inside—has proven insufficient against modern threats.
The answer to this reality is the Security Operations Center (SOC)—a centralized operational structure serving as the foundation of a modern defense strategy. A SOC is a complex ecosystem where people, processes, and technologies are interwoven into a single organism aiming to ensure continuous visibility, detection, and response to incidents in real-time, 24/7/365.
In this article, I will present a comprehensive picture of a modern SOC—from team architecture and analyst psychology, through technical details, to the regulatory requirements of the NIS2 directive and a vision of a future based on artificial intelligence.
A Security Operations Center is a physical or virtual location where a team of cybersecurity experts continuously monitors, detects, analyzes, and responds to security incidents. A SOC is not merely a "fire brigade" putting out fires that have already started. Modern centers are evolving into proactive risk management hubs, utilizing advanced analytics and Cyber Threat Intelligence (CTI) to predict attacks before the adversary executes the first command.
A common mistake is confusing a SOC with a NOC (Network Operations Center). The difference is fundamental:
In light of the increasing aggressiveness of cybercriminals and regulations like NIS2, the SOC is becoming a key element of Business Continuity. Without it, in the event of a ransomware attack or a serious breach, an organization may simply cease to function. A SOC is no longer a luxury reserved for the largest banks, but an essential survival element for every digital organization.
Paradoxically, the greatest threat to SOC effectiveness is not a lack of technology, but the burnout of analysts standing on the front lines of defense. You can own the most expensive software in the world, but without qualified and motivated people, it is just an expensive screensaver.
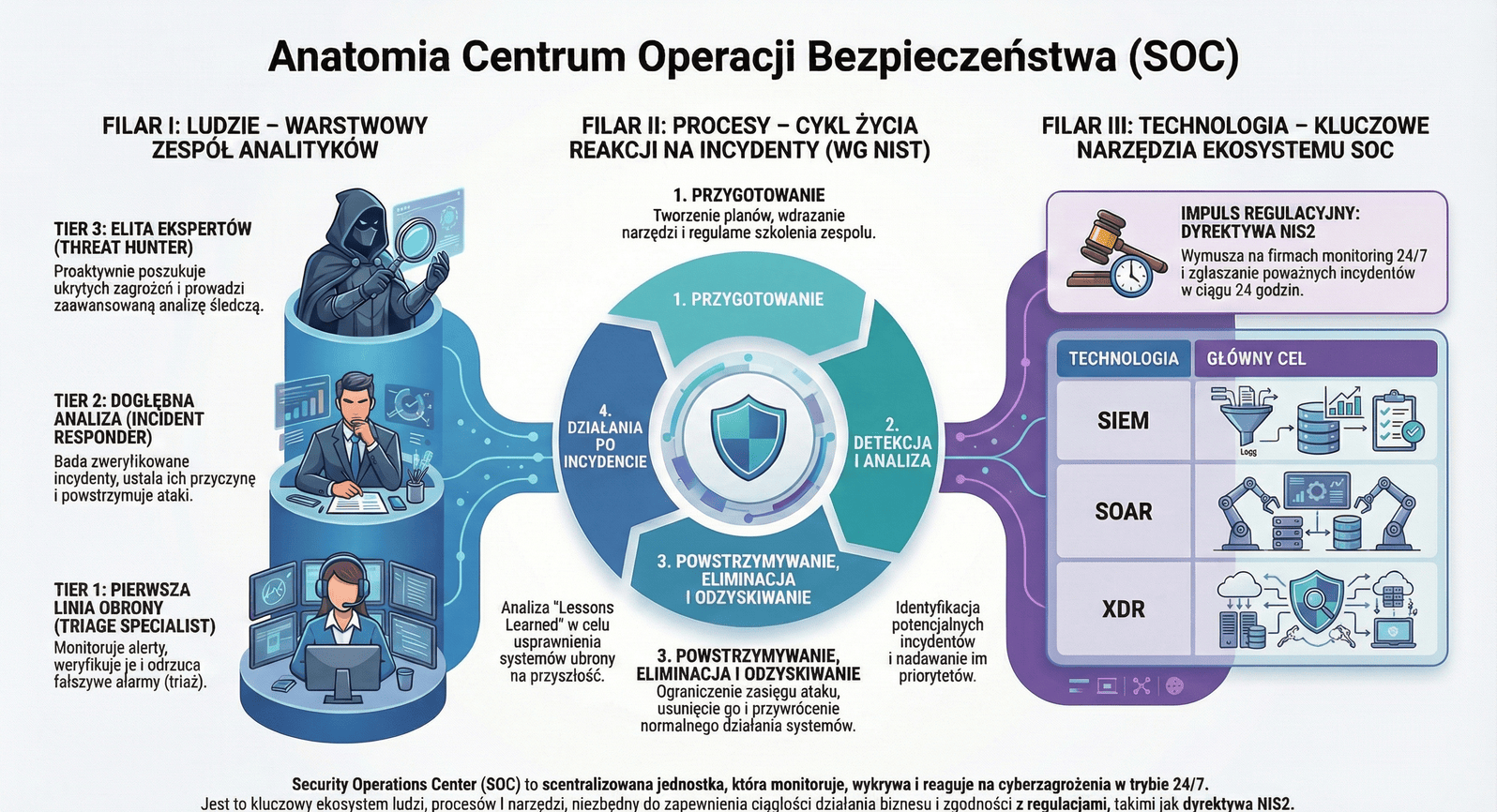
The organizational structure of a SOC is typically based on a Tier-Based Model, which allows for managing the chaos of thousands of daily alerts through a division of responsibility and incident escalation.
This is where every alert generated by monitoring systems lands. Tier 1 analysts constitute the "infantry" of cybersecurity.
Tasks:
Challenges:
Biggest Risk: Alert Fatigue
The key threat is the phenomenon of "alert fatigue." Analysts bombarded with thousands of notifications daily, most of which turn out to be irrelevant, lose vigilance. This dramatically increases the risk of overlooking that one critical incident that could paralyze the entire organization.
When Tier 1 determines that something requires deeper analysis, the incident is escalated to Tier 2. These specialists possess deeper technical knowledge and greater autonomy.
Tasks:
Actions:
The best of the best. Tier 3 analysts do not wait for alerts. Their work is based on the assumption that an advanced adversary may already be in the network but remains invisible to automatic detection systems.
Tasks:
Role:
The SOC Manager must bridge two worlds: technical and business. They are responsible for:
Industry data is disturbing:
70% of SOC analysts experience symptoms of burnout, and many plan to change jobs within the next year.
Causes:
Strategic Consequences:
The key to solving the staffing crisis is:
It is a popular belief that a SOC deals mainly with responding to active attacks—"putting out fires." In reality, the effectiveness of a security operations center depends most on the work done long before any incident is detected.
The fundamental process structure in any mature SOC is the incident response life cycle described in the NIST standard. It consists of four main phases:
Counterintuitively, preparation, not reaction, is the foundation of SOC effectiveness.
Key elements of the preparation phase:
1. Asset Management
2. Tool Implementation and Configuration
3. Creation of Playbooks (Procedures)
4. Training and Tabletop Exercises
Containment:
Eradication:
Recovery:
A mature SOC spends most of its time on proactive preparation, improving procedures, and strengthening defenses, rather than on reactive action in crisis mode.
Possessing the most modern and expensive security tools does not guarantee protection. Technology becomes a trap if it is not part of a larger plan involving qualified people and defined processes.
The technological core of a modern SOC relies on three pillars: SIEM, EDR/XDR, and SOAR. Each plays a different, complementary role.
Functions:
Correlation Example: A SIEM can link a failed VPN login with a strange permission change in a database and shout: "We have a problem!" – identifying potential privilege escalation.
Drawbacks:
EDR (Endpoint Detection and Response):
XDR (Extended Detection and Response) – "EDR on Steroids":
SOAR is a life-saving technology for analysts. It automates repetitive, manual tasks and integrates ("orchestrates") various tools so they can act as one cohesive system.
Example Phishing Automation Flow:
Benefits:
| Feature | SIEM | SOAR | XDR |
|---|---|---|---|
| Main Goal | Log management, compliance, historical analysis | Automation, orchestration, case management | Integrated real-time detection and response |
| Data Source | Any logs (wide range) | Alerts from other systems | Telemetry from sensors (deep context) |
| Role in SOC | Analytical "Memory" and "Brain" | Executive "Hands" | "Next-Gen" detection operational platform |
| Relationship | Source of alerts for SOAR | Action executor for SIEM/XDR | Often replaces SIEM in detection, but not in compliance |
Technology is useless without qualified people to operate it and defined processes (Playbooks) that steer it.
SOAR is becoming the key binder that allows people and processes to effectively utilize the potential of SIEM and XDR. It solves the information overload problem, which is the direct cause of analyst burnout.
The decision on how to deploy a SOC is not a technical issue, but one of the most important strategic and financial decisions for an organization.
Description: Building your own security operations center from scratch.
Pros:
Cons:
For whom: Large organizations with very specific requirements (e.g., government institutions, large banks) or entities that cannot outsource security functions due to regulatory reasons.
Description: Outsourcing monitoring and incident response to a specialized external provider (MSSP – Managed Security Service Provider).
Pros:
Cons:
For whom: Small and medium-sized companies, organizations without a budget for their own SOC, companies wanting to quickly meet compliance requirements (e.g., NIS2).
Description: Combining an internal team with the services of an external provider.
Typical division of responsibility:
Pros:
Cons:
For whom: Mid-sized organizations that want to retain control but do not have the budget for a full in-house SOC operating 24/7.
Most companies should not build their own 24/7 SOC from scratch. The hybrid or managed model is often the most balanced solution, allowing for control retention while optimizing costs and protecting the team.
The necessity of having a SOC function has ceased to be a voluntary choice and has become a legal obligation for thousands of Polish companies.
The EU NIS2 (Network and Information Security 2) directive is being implemented in Poland through the amendment of the Act on the National Cybersecurity System (KSC). This regulation fundamentally changes the rules of the game in the cybersecurity area.
The new law divides entities into two categories:
Essential Entities:
Important Entities:
It is estimated that the regulation will cover several thousand Polish companies – significantly more than before.
A key innovation of NIS2 is the emphasis on supply chain security. Organizations are responsible for the cybersecurity of their key ICT suppliers, extending the scope of responsibility beyond their own walls.
The most radical change concerns reporting serious incidents to the appropriate CSIRT bodies (NASK, GOV, MON):
Key Thesis:
If a serious incident is detected on Friday evening, during the weekend, or on a holiday, an organization without round-the-clock monitoring has no chance of meeting the 24-hour deadline.
An organization that does not have analysts on duty at night or during holidays will not be able to meet this requirement, exposing itself to:
In this way, the NIS2 directive de facto forces hundreds of Polish companies to have a SOC function operating in 24/7/365 mode. This is a huge operational and financial challenge, forcing organizations to strategically rethink their security model.
An example of successful adaptation to NIS2 is Atman, a data center market leader in Poland. Facing new regulatory requirements, they implemented a SOC service based on the SecureVisio platform (SIEM/SOAR). The goal is real-time risk analysis, automation of response, and full compliance fulfillment while optimizing costs.
The traditional metric of "number of closed tickets" is insufficient to assess SOC effectiveness. A modern security operations center should be evaluated through the prism of metrics that actually translate into business risk reduction.
What it measures: How quickly the SOC detects an active threat from the moment it occurs.
Why it's important: The faster the detection, the less time the adversary has for data exfiltration or spreading within the network.
Goal: Minimizing MTTD through advanced analytics, CTI, and threat hunting.
What it measures: How quickly the SOC responds to a detected threat and neutralizes it.
Why it's important: In the age of ransomware, where an attack can encrypt an entire network in hours, response time must be counted in minutes, not hours.
Goal: Response automation via SOAR to reduce MTTR to a minimum.
What it measures: How long an advanced adversary (APT) remained in the network unnoticed, from the moment of initial compromise to detection.
Why it's important: The longer the Dwell Time, the greater the probability of data theft, backdoor installation, and deeper compromise.
Industry benchmark: According to reports, the global average Dwell Time is several dozen days. A mature SOC aims to reduce this time to a few days or hours.
What it measures: What percentage of alerts generated by systems turns out to be false positives.
Why it's important: An excessively high False Positive Rate leads directly to alert fatigue and analyst burnout.
Goal: Continuous tuning of SIEM rules and using XDR/AI to reduce false alarms.
What it measures: What percentage of incidents is fully closed (investigation, containment, eradication, recovery) within a specific time.
Why it's important: Measures the completeness of the incident response process.
The future of security operations is autonomization. The Autonomous SOC concept assumes that artificial intelligence (AI) and hyper-automation will take over most tasks currently performed by Tier 1 and Tier 2 analysts.
What AI will take over:
Intelligent AI agents will independently:
Does this mean the end of jobs for people? Quite the opposite.
The role of humans in SOC is evolving towards tasks where we are irreplaceable:
Technological evolution is accompanied by organizational evolution. A Cyber Fusion Center is a concept involving:
Integrating experts from various domains in one place:
Benefits:
Example: An attempt at unauthorized entry into a server room (physical security) correlated with a simultaneous brute-force attack on administrator accounts (cybersecurity) reveals a coordinated attack of the insider threat or physical penetration type.
The future of SOC is the symbiosis of human creativity, strategic thinking, and ethical judgment with the speed, scale of analysis, and precision offered by artificial intelligence.
A Security Operations Center (SOC) is a centralized organizational unit responsible for continuous monitoring, detection, analysis, and response to cybersecurity incidents 24/7/365. A SOC combines people (security analysts), processes (playbooks and procedures), and technologies (SIEM, EDR, XDR, SOAR) into a single protection ecosystem.
SOC (Security Operations Center) focuses on security - detecting threats, anomalies, and cyberattacks. NOC (Network Operations Center) looks after network performance and availability - uptime, bandwidth, infrastructure monitoring. SOC looks for enemies, NOC ensures system efficiency.
Building your own 24/7 SOC requires a minimum of 10-12 full-time employees (considering shifts, vacations, and training), which generates costs of at least several million PLN annually. Added to this are costs for software licenses (SIEM, EDR, XDR - often 100-500k USD/year), infrastructure, and physical space. Therefore, most companies choose the managed SOC (SOCaaS) or hybrid model.
Managed SOC, also known as SOCaaS (SOC as a Service), is an outsourced security operations center model. A specialized provider (MSSP) ensures 24/7 monitoring, incident response, and access to experts in a subscription model. Deployment takes weeks instead of months, and costs are significantly lower than for an in-house SOC.
Key technologies include:
Alert Fatigue is a phenomenon where analysts bombarded with thousands of notifications daily (mainly false alarms) lose vigilance and start ignoring alerts. This leads to overlooking critical incidents. Studies show that 70% of SOC analysts experience burnout, which is the biggest threat to operations center effectiveness.
Threat Hunting is proactive hunting for threats conducted by Tier 3 analysts. Unlike reactive response to alerts, threat hunters assume that an advanced adversary is already in the network but remains invisible to automated systems. They use advanced analysis techniques, forensics, and intuition to detect hidden threats.
The NIS2 directive, implemented in Poland by the amendment of the KSC Act, requires essential and important entities to report serious incidents within 24 hours (early warning) and 72 hours (full notification). In practice, this means the necessity of having 24/7/365 monitoring, as without it, meeting these deadlines is impossible. Penalties are up to 10 million EUR or 2% of annual turnover.
A hybrid model combines an internal team with the services of an external provider. Typically: an external MSSP provides Tier 1 monitoring in 24/7 mode (especially nights and weekends), while the internal team (Tier 2/3) conducts advanced analysis, threat hunting, and strategy during business hours. This is a cost-optimal solution protecting own experts from burnout.
SIEM is a security event management system - it collects logs from all sources, correlates them, and generates alerts. Great for compliance and historical analysis, but generates many false alarms. XDR (Extended Detection and Response) is an integrated platform combining telemetry from endpoints, network, cloud, and identity. It offers higher quality alerts thanks to deeper context and reduction of false positives. XDR often replaces SIEM in detection, but not in compliance.
It depends on the model:
These are key KPI metrics measuring SOC effectiveness. Additionally, Dwell Time (time an intruder spends in the network unnoticed) and False Positive Rate (percentage of false alarms) are monitored.
Yes, especially in light of NIS2. However, small and medium-sized companies should not build their own SOC due to costs (millions of PLN annually) and recruitment difficulties. Optimal solutions are:
The Security Operations Center has ceased to be a technological toy for the wealthiest corporations. In light of the aggressiveness of modern cybercriminals, regulations like NIS2, and the inevitable development of artificial intelligence, the SOC has become an element of survival for every digital organization.
The biggest threat is not the lack of technology, but the burnout of people standing on the front lines of defense. Alert fatigue destroys the effectiveness of even the best-equipped SOC.
The best defense is built before the attack, not during it. The Preparation phase in the incident life cycle is the most important.
Technology without people and processes is a trap. SIEM, XDR, and SOAR are powerful tools, but their effectiveness depends entirely on qualified analysts and well-defined playbooks.
Building your own 24/7 SOC is a million-dollar decision that most companies should not make hastily. The hybrid or managed model is often the most balanced solution.
The NIS2 directive de facto forces the possession of a SOC function operating in 24/7/365 mode on thousands of Polish companies, under threat of penalties reaching 10 million EUR or 2% of turnover.
The future is autonomization, where AI takes over routine tasks, and people focus on strategy, threat hunting, and algorithm management.
Considering these challenges and trends, is your organization's approach to security a relic of the past, or is it ready for the future that has just arrived?
Regardless of whether you build a SOC yourself, hire an external provider, or choose a hybrid model – one truth remains unchanged:
It is not the technology that is most important, but the people and processes that steer it.
If you are considering implementing a Security Operations Center in your organization or want to optimize existing security processes, contact us - we will help choose the optimal solution tailored to your budget and regulatory requirements.
#SecurityOperationsCenter #SOC #Cybersecurity #NIS2 #SIEM #XDR #SOAR #ThreatHunting #IncidentResponse #ManagedSOC #SOCaaS #CyberThreatIntelligence #AlertFatigue #MTTD #MTTR #SecurityManagement #DataProtection #Compliance

Chief Technology Officer at SecurHub.pl
PhD candidate in neuroscience. Psychologist and IT expert specializing in cybersecurity.

A comprehensive guide to SIEM transformation. From data normalization, through the "Pyramid of Pain", to analyst psychology. Learn how to go beyond simple signatures and start detecting behaviors.

A 24/7 in-house SOC requires 5-6 analysts per position and costs 5x more than you think. Discover 4 critical mistakes when choosing an MSSP, the MSP vs MSSP difference, the truth about "15-minute response" and why outsourcing doesn't absolve management from NIS2 responsibility.

SOC analysts are drowning in a data flood, wasting hours on false alarms. Is 2025 and the arrival of autonomous AI agents the moment machines finally let humans stop "chasing ghosts" and start thinking strategically?
Loading comments...