Let's see how we can help you!
Leave a message and our dedicated advisor will contact you.
Send us a message
0/10000
Leave a message and our dedicated advisor will contact you.

Polish cyber defense is a system with two faces. On one side, we have the new, official cyber.gov.pl website, designed to organize information chaos and offer free tools to citizens. On the other—in the shadows of offices and server rooms—an intelligence game is being played, in which Poland officially admits for the first time to possessing offensive "cyber weapons."
We hear about data leaks and phishing every day. The Ministry of Digital Affairs indicates that in 2025, the number of handled incidents rose to over 220,000 (an increase of over 100% YoY). In response to this threat, the state is building a security architecture that is far more complex than headlines suggest. We discover what this duality looks like in practice: from tools available to the average citizen, to a deterrence strategy rarely discussed in the news.
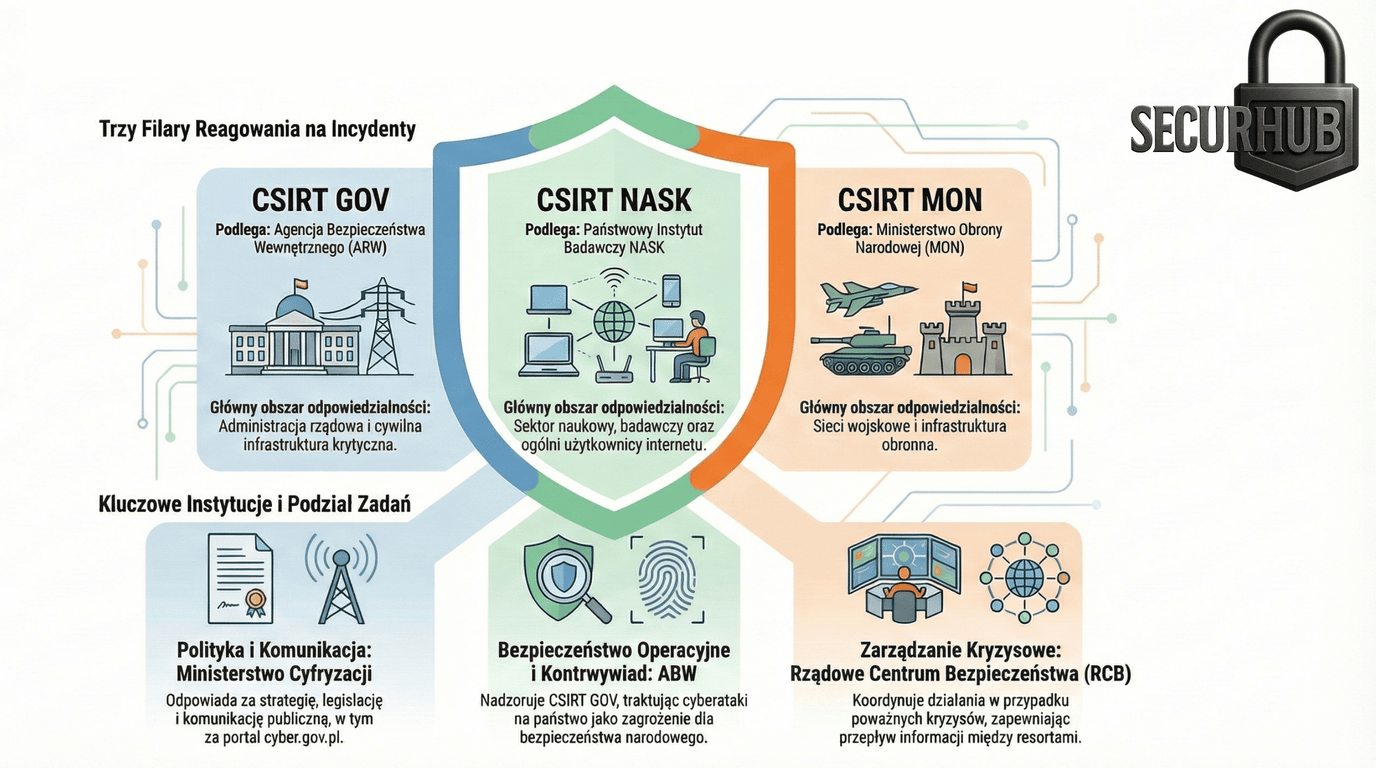
To understand Polish cybersecurity, one must recognize its intentional division into a public (civil) zone and a classified (state) zone. This is not just a matter of bureaucracy, but a fundamental defense strategy.
cyber.gov.pl portal. It focuses on the cyber hygiene of citizens and companies.Key difference: By placing CSIRT GOV within the structures of counterintelligence (ABW), a serious incident in the state sphere triggers immediate investigative and attribution capabilities. This is a strategic advantage over purely civilian models.
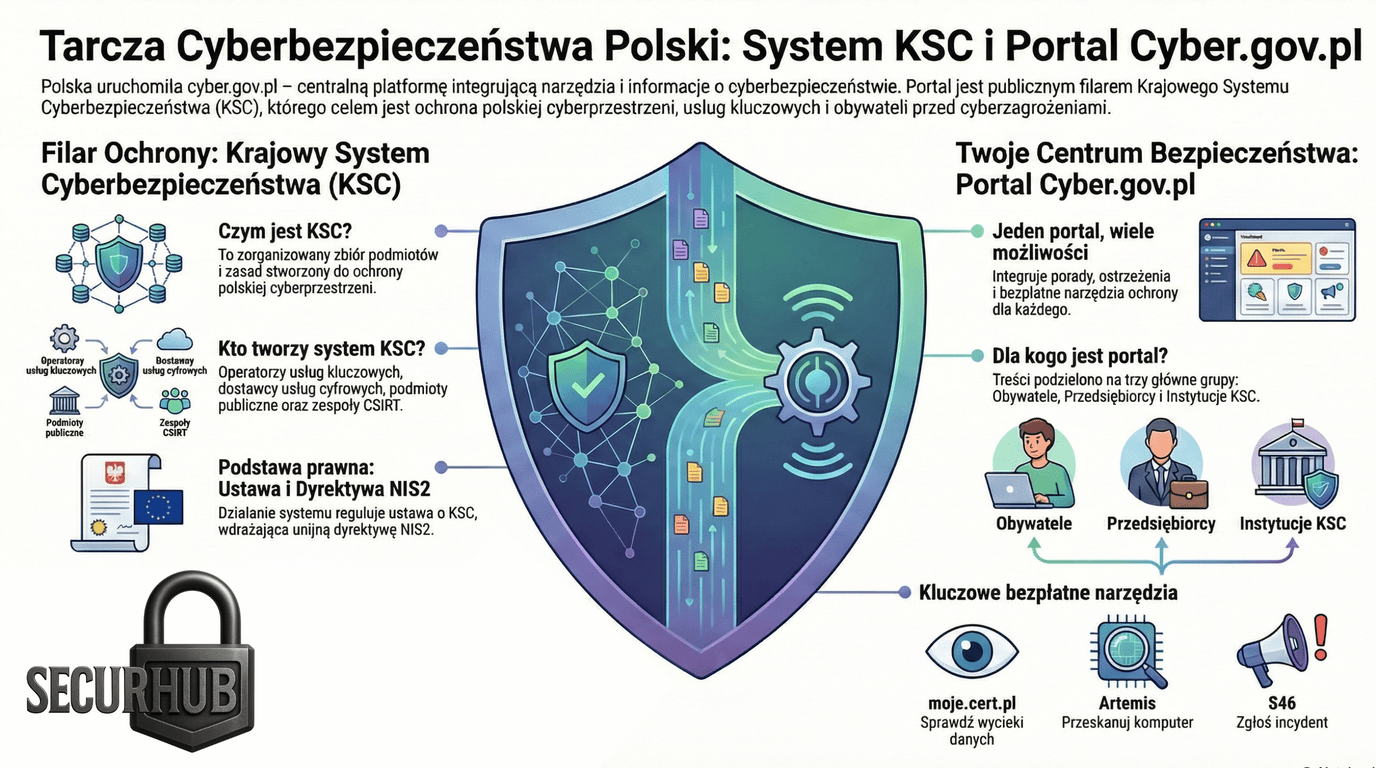
cyber.gov.pl?In response to the fragmentation of information regarding threats, the government launched the cyber.gov.pl portal. It is intended to be a "single address" allowing control over the chaos of disinformation and cyber threats. Instead of seeking help on forums, citizens and companies are to receive verified knowledge in one place.
The portal's creators divided it into zones to precisely target different audience groups:
| Target Group | What does the portal offer? |
|---|---|
| Citizens | Data protection guides, fraud warnings, education (e.g., how to create secure passwords). |
| Entrepreneurs | Knowledge on securing company infrastructure and business continuity. |
| Institutions (KSC) | Incident reporting tools, compliance guidelines for the NIS2 directive, and access to the S46 system. |
The greatest value of the portal—appreciated even by skeptics—lies in the concrete, free tools developed by entities like CERT Polska, which allow users to move from theory to practice:
Although cyber.gov.pl is a step toward organizing the ecosystem, the initiative has met with a cold reception from some experts. While the official narrative speaks of a "centralized platform," critics point to "minimalism and superficiality."
The main allegations concern:
This dissonance between the promise of a "trusted platform" and allegations of it being a facade creates a trust gap that is dangerous during times of crisis.
The most surprising piece of the puzzle, rarely discussed in the context of free antivirus scanners, is the shift in Poland's war doctrine.
The Minister of Digital Affairs officially confirmed to Puls Biznesu that Poland possesses an offensive "cyber weapon." This is a fundamental change:
Poland sends a clear signal to allies and adversaries: we will not be just a shield. We are ready to impose real costs on an attacker, operating across the full spectrum of cyber conflict.
Polish cyber defense is a complex mechanism. On one hand, the state extends a hand to the citizen, offering basic protection tools via cyber.gov.pl—an initiative that is necessary, though still requiring refinement and integration (e.g., with the National Node). On the other hand, behind the scenes, ABW and CSIRT GOV are sharpening a digital sword, ready for offensive actions that most of us will never hear about.
The key to security in the coming years will not only be the strength of our secret cyber weapons but, above all, whether the public "shield" in the form of an aware society and efficient e-services proves not to be full of holes.
It is a central government portal that aggregates cybersecurity information for citizens, entrepreneurs, and institutions. It is meant to be a "single address" for verified knowledge about threats and protective tools.
The most important ones are moje.cert.pl (checking for password and email leaks), Artemis Scanner (detecting vulnerabilities in websites), and Safe Mail (verifying suspicious messages).
Yes. The Minister of Digital Affairs officially confirmed that Poland possesses offensive capabilities and can conduct a retaliatory strike on an aggressor's infrastructure in response to a cyberattack on critical Polish systems.
CERT Polska (NASK) operates in the public and educational layer, providing tools for citizens and companies. CSIRT GOV reports to the ABW (Internal Security Agency) and protects the state's critical infrastructure, operating within the sphere of counterintelligence.
Aleksander

Chief Technology Officer at SecurHub.pl
PhD candidate in neuroscience. Psychologist and IT expert specializing in cybersecurity.

The NIS2 Directive is not just another GDPR - it`s a cybersecurity revolution with personal board liability and penalties up to 100 million PLN. Discover if your company is covered and how to avoid severe sanctions.

The release of the mObywatel source code was supposed to be a celebration of transparency. Instead, we got a lesson in "malicious compliance," right-click blockers, and proof that the Polish administration still confuses security with secrecy.

Learn everything about the Security Operations Center (SOC) - from team building, through SIEM/XDR/SOAR technologies, NIS2 requirements, and deployment models, to the future with AI. A practical guide for CISOs and IT managers.
Loading comments...